In Part 1, we talked basic computer science. I highly recommend reading/re-reading Part 1 before reading this article if you don’t have a firm grasp on the basics of computer science.
We’re going to start here in Part 2 by talking generically about some of the hurdles that cryptocurrencies have had to overcome, then we’ll define some terms, and finally we’ll put all the pieces together into a basic model of how a blockchain-based cryptocurrency works.
Traditional Ways of Passing Data through an Untrusted Medium
Let’s do a quick survey of a few ways that important data can be passed through an untrusted medium (i.e. the Internet). You’ll recognize some of these from Part 1.
Encryption
Pretend you have a secret message that you want to send from your computer to your friend’s computer. An easy example may be a message including your credit card information to purchase Glibertarians pink footie pajamas. How do you send that information from your computer, through a bunch of network devices (routers, switches, etc.) that are owned by neither you nor your friend, and to your friend without being intercepted by a nefarious third party?
The easy answer is cryptography. Let’s change the message in a way that only your friend has the “key” to unchange it. There are many ways to do this, but one of the most common is public key cryptography. If you want more info on public key cryptography, check out Part 1.
Secured Channels
Sometimes, you’re sending a bunch of secret information across the network to the same place. The most common example is when you’re working from home. You’re transacting a bunch of secret information with your corporate servers, and it may be easier to just establish a secure channel between your computer and the corporate network so that you don’t have to manage the overhead of encrypting the info piecemeal. What am I describing? VPN.
This doesn’t really have anything to do with blockchain, but it gives you a bit of context about how security can be implemented over the Internet.
Trusted Authorities
Trusted authorities also have nothing to do with blockchain, except to act as an opposing contrast to the way blockchain works. We talked in Part 1 about the two ways that public key cryptography can be used. One way is to securely send secret information across an untrusted link. Another way is to sign a message and validate that the message came from the person you think it did.
What if I want to know that you’re legit before I send you all my personal information? STEVE SMITH could easily insert himself between you and me, send me his public key, and then intercept and decrypt my response. This is called a “man in the middle” attack. Rather than just trust that the public key you supposedly sent me, I can reach out to a trusted 3rd party, who has your public key on file. I request your certificate from this trusted 3rd party (called the Certificate Authority), and compare the public key in the certificate with the public key you sent me to make sure it hasn’t been meddled with. The weakness of this method is that you have to trust the security of the Certificate Authority (the most well known CA is VeriSign).
Blockchain uses some of the encryption technologies we have discussed, but specifically cannot use VPN or CA technology because blockchain is implemented in a completely trustless environment. Why is it a trustless environment? Because authority is distributed rather than centralized.
Centralized, Decentralized, and Distributed: A Libertarian Way to Organize Things
I’m going to keep this focused to the tech realm, but y’all are smart enough to expand these concepts outside the realm of computers. There are three main ways of organizing tech in order to accomplish a task. Centralized systems involve everybody reaching out to one single node (e.g. server or cluster of servers) in order to accomplish the task. Decentralized systems involve everybody reaching out to one of a small number of nodes in order to accomplish the task. Distributed systems involve everybody reaching out to everybody else in order to accomplish the task.
Centralized
Centralized systems are what we use on an everyday basis. I want to buy something from Amazon, so I connect to an Amazon server and make the purchase. You want something from Amazon, so you connect to an Amazon server and make your purchase. This is a centralized system*, everybody connects with an Amazon server in order to complete their transaction.

* You could argue that Amazon runs a decentralized system, because there are Amazon servers all around the world to share the load of so many people shopping simultaneously. However, for this description, “centralized” refers to only one “entity” being involved, no matter the number of physical servers.
Decentralized
Decentralized systems are less common, but are still used on a regular basis. I want to refinance my house, so I go to LendingTree or any one of the other online insurance brokers. I input my information, which is sent to a handful of banks and other lenders, and each lender returns the request individually. If one lender doesn’t respond, it’s not quite as efficient, but I still have access to all of the other lenders.

Distributed
What if we take it a step further? Rather than a handful of entities, everybody can be an entity and everybody interacts with everybody. For example, Uber. You submit a ride request, and other people choose whether or not they want to fulfill that request. Uber isn’t perfectly distributed, as there is a barrier to entry before you can drive for Uber, but the barrier is low enough that it’s essentially distributed for our purposes.

How Transactions are Verified when Nobody can be Trusted
We have two obstacles to get over before we can verify a transaction. The first obstacle is ensuring that nobody has stepped in and altered a legitimate transaction. The second obstacle is ensuring that legitimate creator of the transaction isn’t trying some funny business.
We’ve already discussed a method for tackling the first obstacle, using public key signing. The person who is giving the money signs the transaction with their private key, and the public key is included in the transaction data. Then, anybody in the public can check the signature using the public key to make sure that the transaction was approved by the originator.
What about the second obstacle? Well, that’s a little more complicated and involves some economic incentives. We’ll get into this in more detail in Part 3 of this series, but suffice it to say that pulling off a con to steal somebody’s cryptocurrency involves an impossibly large amount of computer resources, and an immense amount of luck. The incentive to steal is way overridden by the costs of acquiring the raw processing power required to make such a con even remotely possible.
How does bitcoin get stolen, then? Usually some currency exchange website is hacked, and the private keys of users’ accounts (wallets) are compromised. It’s not a flaw in cryptocurrency, but in the exchange’s security. Blaming such hacks on cryptocurrency is like blaming the US Dollar because Chase’s system gets hacked.
Definitions and Terms of Art
Blockchain (Sometimes called distributed ledger technology) – A list of connected messages that contain transaction information. The blockchain is copied to every node (computer) in the blockchain network, allowing each and every participant in the blockchain to examine the blockchain for inconsistencies.
Cryptocurrency – A financial product that is transferred between people using a blockchain. Some people view cryptocurrencies as investment products (commodities). Others view cryptocurrencies as a currency. Many cryptocurrencies use a mathematical algorithm for “printing” new money that is rather deflationary, making them attractive long term investment vehicles.
Bitcoin – The original cryptocurrency that is trading for somewhere in the neighborhood of $11k per Bitcoin at the time of writing. You don’t have to buy full Bitcoins, but can buy as little as 0.0000001 Bitcoin.
Smart Contract – Some uses of blockchain are less tightly coupled to currency. Ethereum, for example, is a broader use blockchain system, and includes smart contracts, which are publicly inspectable contracts that are mostly self-executing. For example, if getting the wifi password is keyed to paying your rent, the smart contract will retain the new month’s wifi password and will not release it to the tenant until rent is paid.
Fork (of blocks in a chain) – A condition of the blockchain where two blocks are created and verified by different nodes in the network at substantially the same time. In such a situation, there is a “fork” until the next block is verified. Whichever forked block is retained by the node that verified the next block is the “winner”, ending the “fork.”
Fork (of cryptocurrencies) – A split off of a new cryptocurrency from an old one. Usually this happens because the older cryptocurrency has some limitation or flaw that the new cryptocurrency resolves. Depending on the specific situation, the older currency may transform into the new currency.
Merkle Tree – A type of binary tree (a hierarchical linked list where a “parent” node has at most two “children”) used to organize the cryptocurrency transactions stored within a block. Each leaf node (i.e. nodes without children) of the Merkle tree represents a transaction, and the parent nodes represent a combination of multiple transactions. Each node has a hash, with the root node (the parent of all parents) containing a transaction hash for the entire block. These hashes can be used to verify the accuracy of the transactions, and the transaction hash for the entire block is used in creating the hash for the block.
Wallet – A data structure built around a user’s private key that retains all of the cryptocurrency that has been transferred to it.
Exchange – A website that retains a cryptocurrency wallet for each of its users. Exchanges are like a cross between a bank and an investment broker.
Blockchain? Is That Some New Type of Jewelry?
Blockchain is the technical underpinning of cryptocurrencies. A blockchain is a linked list of data structures. Each data structure includes a header, a transaction ledger, and a pointer to the prior block.
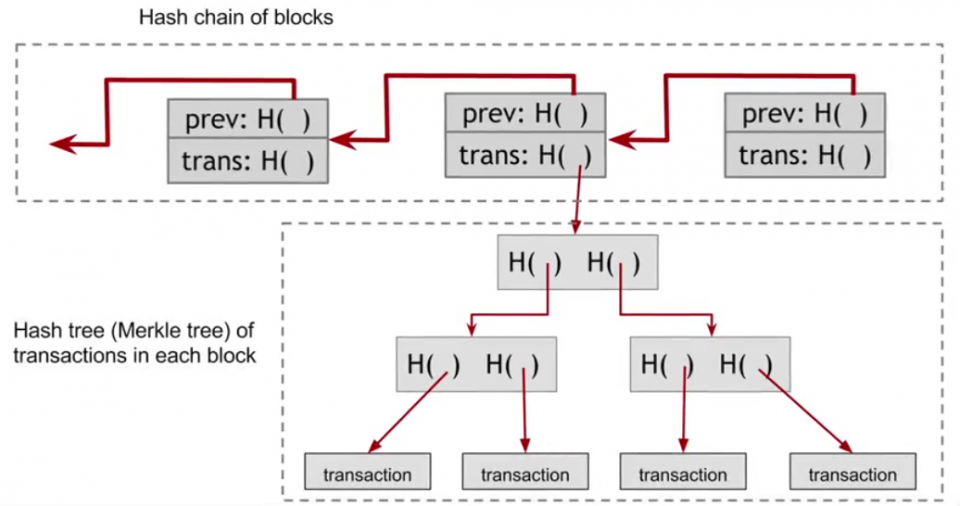
Here is a very high-level view of what a blockchain looks like. You have ledger of transactions arranged in a tree form (a tree is a linked data structure kind of like a linked list, but with more than one relationship saved in the structure. For example, in a binary tree, each “parent” data structure has two “children”). The actual transactions are located in the leaf nodes (a leaf node has no children), and the root is the top parent node. The Merkle tree (the specific type of binary tree used for blockchain transactions) calculates the hash of each transaction, and then continues to hash the combined hashes up the tree until we get what’s called the Merkle root hash (shown as “trans: H( )”). The specifics of how all this works isn’t super important, and it’s fairly intuitive once you understand hashing. You’re essentially taking hashes of hashes until you get one single hash that represents all of the transactions in the block. Why do we want that?
Because the hash of the block (used for security/verification purposes) isn’t the hash of the ENTIRE block, but only of the header of the block. The actual transactions and the Merkle tree are contained in the transaction ledger, and are not taken into account when calculating the hash of the block. However, the Merkle root hash (which takes into account all of the transactions) is located in the header of the block and is thus taken into account when calculating the hash of the header of the block. If a nefarious actor tried to change one of the transactions to route currency to his wallet, it would change the Merkle root hash, which would change the hash of the block, resulting in it being obvious to the blockchain network that something has been tampered with. We’ll go into more detail on this in Part 3 of the series.
The last concept I want to bring up in this article is the increasing security over time. How does that work? Well, it has to do with the linked list of blocks. Let’s say we have three blocks that STEVE SMITH wants to corrupt in order to steal some cryptocurrency.
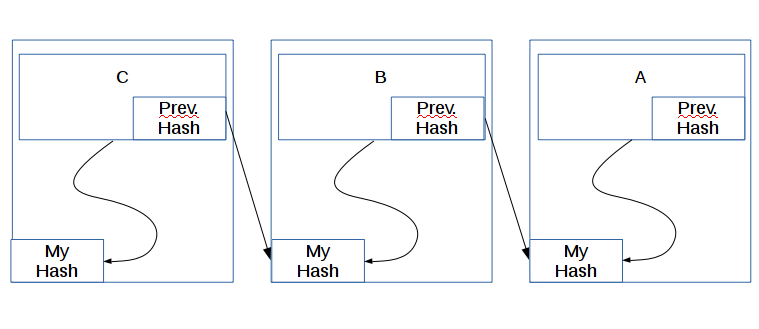
STEVE SMITH will have the easiest time corrupting block C. Why? Because all he has to do is change the transactions and calculate the new hash for C. I say “all he has to do” as if it’s easy. We’ll talk in Part 3 about why this is nearly impossible to do. However, let’s assume for a moment that STEVE SMITH has a ton of computing resources and it isn’t quite nearly impossible to corrupt C anymore. Now, let’s see why the older a block is, the harder it is to corrupt.
STEVE SMITH sees a huge transaction of cryptocurrency in block A and wants it for himself. In order to pull of his heist, he alters the transaction in block A, but now A’s “My Hash” is wrong (we’ll discuss tomorrow how the network knows it’s wrong). STEVE SMITH then spends a bit of time calculating A’s correct new My Hash. Once that’s done, there’s still a problem. B’s “Prev. Hash” is wrong, and the network will see the obvious inconsistency. STEVE SMITH changes B’s Prev. Hash to match A’s My Hash. Great! All fixed!
But wait! B’s My Hash is calculated in part using B’s Prev. Hash, so now B’s My Hash is glaringly wrong. With a sigh of frustration, STEVE SMITH begins the time intensive process of calculating B’s new My Hash. STEVE SMITH, being one of the smartest of his race, sees that block C is going to have the same issue, so he quickly updates C’s Prev. Hash after figuring out B’s My Hash, and begins cranking on C’s My Hash. Finally, after a bit of time, STEVE SMITH has updated the blockchain and his crime was a success!!
Or not. See, while he was cranking hard calculating new hashes for three blocks, the blockchain network was adding new blocks every few minutes (10 minutes for Bitcoin). His fraud sticks out like a sore thumb because blocks D through L all have the wrong hash when his “modified” blocks are included. In order for STEVE SMITH to succeed in his nefarious plan, he would need to control a significant portion of the entire world’s computing power, something on the order of 45% of the blockchain would need to be controlled to give his plan even a dismal chance.
I’m going to stop here. We’re going to dive down to a place where giant octopi and fish with bioluminescent lures live in Part 3. We’ll discuss the details of how hashing is extensively used in the blockchain, how incentives are used to increase security through mining, how blockchain can be used outside of cryptocurrency, a description of the major cryptocurrencies and what they’re useful for, and some of the drawbacks of cryptocurrencies.

These articles help… but damn, I still find a lot of this so confusing.
Thinking about this stuff is optional — the mark of cryptocurrency’s eventual success will be that you need know nothing about it, at all.
Still, for now, it is good to try and gain a little knowledge of the machinery, to help discern when commentary you read on the topic is, as is usually the case, complete BS.
I think that’s a good way of putting it.
Most people who use Bit-Torrent only grasp the mechanics of it because they see its immediate utility; in the process of using it, they end up comprehending some details almost intuitively.
but even BT is effectively a quasi-centralized network; you need to get the ‘maps’ of peer-lists and the torrent files from centralized distribution points. I think people have trouble with the whole “every piece has the seeds of the whole” idea, which forgoes the whole ‘server-client’ thing, and makes every participant a little bit of both.
“the mark of cryptocurrency’s eventual success will be that you need know nothing about it, at all.”
Color me skeptical. The populace at large does not understand how money works and demands socialism.
Maybe I am missing something here, but I am not seeing an explanation on how money works, but more on the security and secrecy of the transactions in a chain. I find that rather fascinating. If either STEVE SMITH and or ELLIOT NESS want to track some transactions there seems to be some very big hurdles and they can’t just nab the accountant and have their way with him/her. There are too many keys involved. Or am I on the wrong train of thought here?
As to how bitcoin works, I don’t get that at all given the very little reading I have done on mining.
If either STEVE SMITH and or ELLIOT NESS want to track some transactions there seems to be some very big hurdles and they can’t just nab the accountant and have their way with him/her. There are too many keys involved. Or am I on the wrong train of thought here?
I don’t exactly know how the FBI broke Silk Road, but my guess is that they siezed Silk Road’s servers and decrypted their local database, which would track transactions and shipments. Match a transaction to a shipment, and you have put a name and address on the Bitcoin wallet.
Oh ya. I forgot about that.
As an accountant who went to a conference where some feds were talking about how they did it, that is pretty much correct, but they can also use the public ledger to find other transactions, and trace those.
The money works on that it takes effort to “authorize” the tokens and transactions… since that takes effort and can’t be created “ex cathedra” it is a limited good and able to behave as “money”. The system limits it..
Why do you accept dollars?.. because the powers that be make it expensive for you to just “make” another dollar.
In these systems the rules make it hard..
It isn’t anonymous… anyone can track the chain.. just that you don’t need to know them.. but yes you can track it and link to physical transactions when people cash out.
I see. There will always be a link between transactions and some other fee/good exchanged even if it is just converting to currency in your bank accoount.
To be viable as a currency, there has to be some means of a vendor verifying that a client has paid for good or services. With cash, that happens when the client physically turns over the markers.
If you eliminate the link, the “currency” is useless, because the seller needs to be able to tell who has paid and who hasn’t.
Worth stressing that this is really the defining characteristic of the system — that it doesn’t care about your identity, and instead cares only about the fact that you’ve done work. So the only way to cheat the system, is to do more work than the system; which itself would be counterproductive, since by the act of compromising it, you would make the currency undesirable, undermining the very reason you had went to the work of cheating it, in the first place.
by the act of compromising it, you would make the currency undesirable, undermining the very reason you had went to the work of cheating it, in the first place.
Depends on what other things you gain by doing it. And even if it is counterproductive in the long run, it may be beneficial in the short term. The Spanish collapsed their own economy by extracting too much gold; the idea that they shouldn’t devalue their own money by creating too much of it didn’t enter into the equation until it was way too late.
Fair point. “We must not allow a mine shaft gap!”
“Maybe I am missing something here”
Perhaps you missed the word “deflationary”.
I also don’t see the value in taking security for granted. Obviously we’re reading this article so we aren’t taking it for granted, it just seemed like a poor reply to Riven’s original comment; 0x90’s reply amounts to “trust me” which sets off my bullshit detector.
???
It seems you must be reading things into what I wrote. To see what I was trying to say, just replace “cryptocurrency” with “the automobile” in my statement.
Interesting that you chose “the automobile” rather than “the city bus” which is a more apt comparison.
I suppose at some level it is amazing that most people on the road tend to know nothing about how automobiles work but can operate one often enough. Yet this same ignorance also winds up enabling the worst drivers and enables those who want more government regulation of the automobile. You don’t need to know general principles of how the automobile works to be a good user of the bus, but that knowledge sure helps you as a user of a Corvair.
Great articles, trshmnstr! I was traveling so just read Part 1 and Part 2.
In Part 1, we talked basic computer science. I highly recommend reading/re-reading Part 1 before reading this article if you don’t have a firm grasp on the basics of computer science.
What the mutherfucken fuck. Homework? *sigh
brb
Yeah, I need to re-read it just to re-familiarize myself with the sorcery he’s yammering on about here.
Sorcery is right. Interesting stuff though. This is stuff I never even think about as I am a computer user who knows how to turn the thing on and little else.
There is a lot of mathematics and CS that you can follow, but couldn’t have thought of as individual ideas. Calculus is obvious when explained…. but getting there from first principles?.. I don’t think I could do it.. I can follow the math, the algorithms .. But I couldn’t have invented them. Relativity? orbital mechanics?
There is a lot of mathematics and CS that you can follow
Says the commenter with DR in their name. I am dangerously close to the retard end of the spectrum when it comes to mathematics.
Nice job. I think you’re striking a good balance, neither glossing over important concepts, nor getting lost in unnecessary technicalities. Not easy.
I am still trying to beat this into my head. I dont follow directions very well. Maybe I should go back and read 1 and 2.
In the mean time I am bringing 5 lbs of catfish filets, a gallon jug of tabasco, a sack of cornbread mix and a deep fryer to my son’s house. We will be busy stuffing ourselves silly with crunchy, tasty, ketchup-drenched catfish. Oh, and lemon wedges. I mustn’t forget those.
Ugh. And the cajun mustard.
I better make a list.
Why doesn’t your son have a deep fryer?
He works 12 hour days as does his wife. They dont cook much. Most of the tools in their kitchen are cargo cult crap. It looks like a knife yet it wont cut anything. It looks like a whisk yet it wont mix anything…etc etc. I have to bring my own tools as well. So far we have bought most of the functional kitchen implements that they have. I guess deep fryer is next on the list.
I suppose that’s a reason.
He can’t afford one due to the tax cuts.
5 lbs of catfish filets, a gallon jug of tabasco, a sack of cornbread mix
Now that sounds good.
The first thing that came to mind was dredging in the mix, a fry and then application of Tobasco.
Not being that good at frying things, I wasn’t sure whether I’d been correct.
Yup. It’s good stuff, and I don’t even like catfish.
Damnit. Just realized I have a frozen pipe in the bathroom. At least it doesn’t seem to have burst.
Nothing a portable heater won’t fix. That sucks though. I have a P-trap in a wall that freezes when we get to far below zero. When that happens I can’t use the washer because it over flows the drain pipe and drains onto the floor.
Along with the portable heater, I would recommend alcohol. For you, not the pipe.
Is that your puppy?
I have to work tonight, so no day drinking 🙁 The only access to the pipe is a crawl space were I don’t trust the wiring enough to leave a heater alone. alcohol will flow when I get back from work though 🙂
Frequent changes of hot towels on the pipe?
the crawlspace is too small to physically access (by me anyway). Meh, it’ll unfreeze at some point, just have keep the pressure out the rest of the system.
Frequent changes of hot towels on the pipe
Yowza!
Nobody needs an anonymous transaction facilitator. Not only do we need to squelch cryptocurrencies, we need to ban cash.
I know your comment was in jest, but of late whenever someone tries to tell me what I don’t need, my reflex is to snidely say “Need has nothing to do with it.”
You guys are a bad influence on me.
Nobody needs 23 different types of currency while children are starving!
Look, if we just issue another currency, eventually we’ll find one that won’t fall to hyperinflation!
It’s being worked on.
TW: NYTimes
Soylent Sauceries?
Cut the fish into finger-wide strips with the grain. Douse the fish generously with tabasco. Squirt a big glop of cajun mustard on the fish. Dust with half of a handful of the cornbread mix and then squish it all around until the fish is coated with a sticky paste. Put the fish pieces in a bowl of the dry cornbread mix and flour them. Pop into the grease at 350F for five minutes.
The cooking kills most of the ‘hot’ from the tabasco but not the pepper flavor. The hot sauce has enough salt in it that you dont have to add any extra. The initial pasting of the fish plus the flouring gives it a generous crust and helps it stick. The cornbread mix (flour plus cornmeal) is extra crispy. If you want it even crispier you could add some dry potato flakes in with your dry mix before flouring.
Squirt cooked fish with fresh tabasco, tartar sauce or lemon juice or ketchup one at a time just before biting. Take your pick. Try not to cripple yourself by eating too much. Oh, and serve with ice water.
You can whip up a pretty good fish fry in just 15 minutes.
I know what conversation this is from… it was just an interesting comment for it to reply to.
Will Ken’s Katfish Kitchen accept currencies of all forms?
Really awesome set of articles!
Question, though:
I’m having trouble wrapping my processor around how a currency which increases it’s volume over time can be deflationary (i.e. increasing the purchasing power of said currency). By making more of it, wouldn’t that naturally reduce it’s purchasing power a la the USD over the last hundred years? What simple concept am I not getting?
Thanks!
By making more of it, wouldn’t that naturally reduce it’s purchasing power a la the USD over the last hundred years? What simple concept am I not getting?
I’ll put a disclaimer on this. I’m not an economist, so this may be completely wrong. However, this is my understanding.
Currency value = amount of currency / objects of value
When the currency value goes up, that’s inflation. When it goes down, that’s deflation. As long as the additional amount of currency is less than the additional objects of value added to the economy, then there’s deflation.
My intuition tells me that you can’t simply sum up the GDP and compare it to dollars printed to determine whether there’s inflation, but I’m not sure how best to quantify that relationship.
Oops, I have that flipped. It’s the opposite.
Currency value = objects of value / amount of currency
When it goes up, that’s deflation. When it goes down that’s inflation.
This is correct. Also, as the currency is accepted by more vendors the number of objects of value goes up.
Deflationary, relative to the value of goods being chased.
Consider the purchasing power of an ounce of gold over some time span, stipulating the artificial condition that all existing gold has already been mined. Each day, each person goes to work, harvesting, improving, and otherwise adding to the value of basic resources, such that relative to the total value of goods in the market, each ounce of gold is seen to increase in value, proportionally. That is to say, with a strictly limited supply of currency, the value of each currency unit will be seen to increase proportional to the increase in the value of goods in the system.
So the question is: how do you wish to define inflation and deflation? In terms of total number of units of currency, or in terms of the purchasing power of each unit? A purely “non-deflationary” or “non-inflationary” currency, i.e. one with a strictly fixed supply, would always increase in purchasing power, as it sat there in your mattress. Which might seem nice from an personal point of view, but it would not serve well as a currency, in terms of society’s need to transact business, and so would either be modified to be somewhat inflationary, or be replaced by a fitter currency.
It was clumsily worded. The finiteness of the number of “new” bitcoins that can be mined is what helps it keeps its value. Gold has a finiteness (not as precise as bitcoin but conceivably finite nonetheless) whereas fiat currency has no conceivable finiteness.
There was talk about setting up a cryptocurrency mining pool – I’m totally down for getting on that action! My girlfriend (my gaming computer) sits around idly most of the time – I should put her to work.
Sweet! I’ll keep you in the loop. I’m trying to figure out what all it’ll take to set up.
I have an old flip phone and a 12 year old Compaq laptop clogged up with porn viruses laying around if they could be put to work.
Some bright soul will build a sexbot that will mine Bitcoins.
*looks for the bitcoin assplug link*
*decides not to pollute browser history with such search terms*
You’re getting smarter. Must be fatherhood, huh?
Yeah, I can’t imagine explaining to Mrs. trshmnstr why I was googling “bitcoin buttplug” while watching the baby.
The bitplug asscoin generator? Work in weed and a Mexican and you are on to something.
Perfect. She’s busy making money while you’re off playing hockey or fishing, then when you come home your bank account is larger and you have a hot sexbot waiting for you. This is the ideal solution to the problem of sexual harassment in the workplace.
Bitcoin-op sexbot sounds easier.
Flip phone and a cash-purchased SIM would come in useful.
Not sure about the laptop though.
I think you should see if you can make a sticky thread or something (maybe just a dedicated thread we can put in favorites), where people who want to participate can post their hardware specs, so we can at least get a rough idea what will be possible.
Can you keep me in the loop as well?
Trshmnstr when you do put the mining team together look at building in spots for people like me who do have the computing power but can help pay for electricity costs.
Maybe there are people with computing power to mine but not cash flow to want to do it.
If so, I want in.
I’m definitely gonna have to get a sense of all the interests involved. I’m also not sure how customizable pools are (without writing one’s own code). However, I’ll get something together in the next month or so where we can all get on the same page. It sounds like I have a ton of reading to do.
I know your comment was in jest, but of late whenever someone tries to tell me what I don’t need, my reflex is to snidely say “Need has nothing to do with it.”
The Bloombergers have been yammering about bitcoin pretty much every time I have turned it on. This morning, there was a piece of an interview with the Bloomberger-in-Chief, former mayor of NYC. He was talking about the need to end privacy and anonymity in financial transactions. Totally serious. Everything must be tracked, regulated and taxed. You cannot parody these people.
Reports on both CNBC and Fox today re: Bitcoin and terrorist funding.
So you end up with both ends of the idiot-spectrum covered.
Who woulda thunk that the toppest of top men would want total control over the people?
Great stuff but let’s just say I’m like Homer not getting he’s Mr. Thompson.
But I think the guys up top were probably right. People don’t really know how banking works and how it relates to how their money is used by banks, checks are cleared etc. Or how a preferred stock actually works or how a money market fund stays fixed. They just…do it. There is a certain amount of trust put into it and we kinda instinctively feel our way around it.
Not too many people tie up your time demanding an explanation as to how calculate interest or the mechanics behind a bond.*
*I had a couple of these people when I was in investments. One guy was so incredibly annoying (‘Yeh but if the price is set at this why does it go like that?’ I’d then answer, and then he’d be all like ‘yeh but if it does do that, how come not in this manner?’ Stuff like that. My boss would always tell me to watch getting suckered into these sort of time wasting vortexes that go nowhere because more often than not people who did that had no intention of buying) I finally had to tell him I’m not a professor in a finance class and that if he was so moved he could go take a securities course or enlist in college.
Money isn’t all that different from electricity. You’ll get all the practical knowledge fairly easily, but the actual underlying physics (in the case of electricity) are a hard slog. In the case of money, it is social psychology. No Christian holds any article of faith as unswervingly as a gold fetishist.
what about those of us who are both?
Not too many people tie up your time demanding an explanation as to how calculate interest or the mechanics behind a bond.*
Every time I see one of those J G Wentworth(?) ads, I start snickering as I imagine them trying to explain net present value to some schmucko with an annuity.
Rather than just trust that the public key you supposedly sent me, I can reach out to a trusted 3rd party, who has your public key on file. I request your certificate from this trusted 3rd party (called the Certificate Authority), and compare the public key in the certificate with the public key you sent me to make sure it hasn’t been meddled with. The weakness of this method is that you have to trust the security of the Certificate Authority (the most well known CA is VeriSign).
FWIW This is not how PKI works on the Internet.
This part: “I request your certificate from this trusted 3rd party” doesn’t happen. Yes, there are trusted third parties known as certificate authorities. And, they probably do keep the certificates they’ve signed in escrow. But you don’t ever issue a request to the CA for a certificate they’ve issued and signed.
Instead, you check the certificate’s self-stated issuer against your list of trusted third parties, then you use your stored copy of the trusted third party’s public key to check the digital signature of the certificate you’ve been given. If the signature is valid, then you know that the CA named in the certificate actually did issue and sign it*. You might also query an OCSP (online certificate status protocol) server or check against an offline CRL (certificate revocation list) to make sure the certificate wasn’t revoked some time after it was issued but before it expired (all certificates have a finite validity period, anywhere from 1 to 10 years depending on various factors).
* = Provided that the mathematics underlying the digital signature algorithm, and the size of keys in use, are still sufficient to support such guarantees against existing technology
Yeah, I should’ve hedged that portion as being based on my (apparently flawed and incomplete) knowledge of the subject.
I’ve learned way more about X.509 than I ever cared or wanted to know, trying to fix all sorts of annoying problems with certificates.
Stalinist pedophile defender repeatedly featured in Reason Magazine has piece in lamestream media arguing that the First Amendment should be abolished because Marxist critical race theorists have decreed that “hate speech causes real harm”.
Then, on Twitter, where the real thinking occurs, something something baitin n inciting.
Oh, yeah, it’s because people don’t disavow Nazis enough. That’s why. Right.
I guess if you can write about sex, immigration, or the campus beat without soiling yourself too much, you can get paid and featured in Reason, regardless of what your other views are. I mean, I don’t absolutely need every member of my libertarian periodical regularly making burnt offerings of in front of a solid gold statute of Ayn Rand with a cigarette in one hand and Atlas Shrugged in the other… but it would be nice.
if you’re a free speech libertarian, what are you going to do about the fact that this argument puts you in solidarity with fascists?
I’m gonna tell you to shove a pair of gardening shears into your scrotum in the hope that you don’t spread your genetic defects.
“Nazis are evil, but free speech protects their victims. I share Noah’s concerns about Nazis,” etc.
It’s like some weird medieval high-court etiquette.
First, you must bow.
Then, you must praise the honored gentlemen.
After, he may deign to let you speak.
Also, before the age of Dalmia, Berlatsky always got eviscerated in the comments. He was an idiot who thought very highly of himself but never bothered to understand any thought that didn’t originate in his own mind.
corrected: before the age of Dalmia, Berlatsky was one of the few writers who always got eviscerated in the comments
“Fascists Coming At Me” is a song i now have to write.
there’s something so incredibly self-important and juvenile in pretending that everyone you disagree with is a “fascist”. Its this idiotic Manichean drama where you are always on the side of Right and Truth and anyone who dares suggest you’re a silly fop is LITERAL HITLER
Commies to the left of me
Fascists to the right, here I am
Stuck in the middle with you.
Free speech exists to protect nazis, you dumbass (not you, src)
To be sure, Nazis are bad, and anyone who stands up for unconstrained speech is enabling the Nazi takeover of America… but… nothing. Burn them. BURN THE NAZIS!
Thanks Trshmnsr. Learning more about blockchain technology is one of those things on my to do list. I keep reading things that lead me to believe this tech is going to be utilized in a way larger scope in the future.
This was a site I had recently bookmarked that talks about future possibilities for the technology.
https://blockgeeks.com/guides/what-is-blockchain-technology/#